IoT Device Management
Easily manage IoT & BLE devices at the enterprise scale with a single, endpoint-agnostic cloud platform.
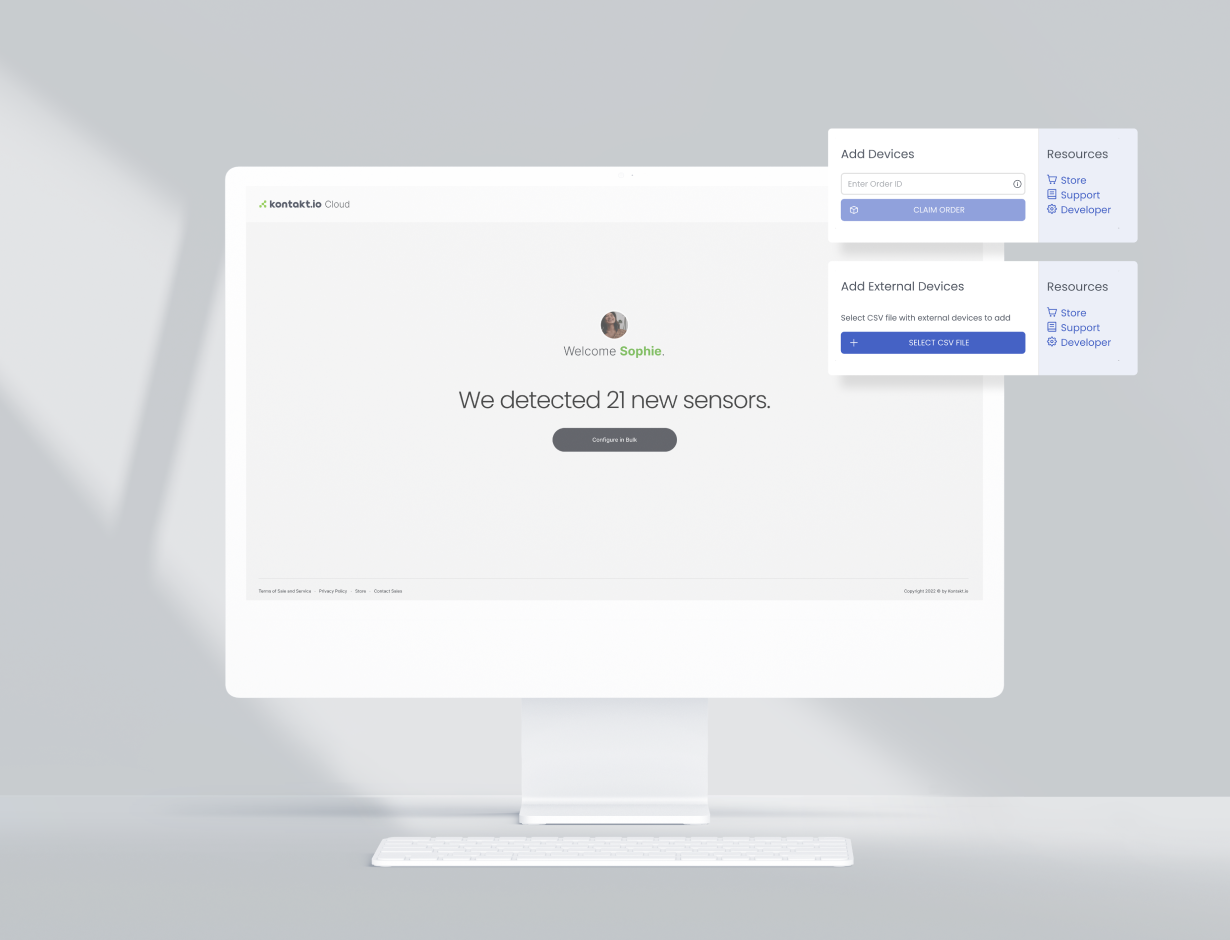
Hospitals use Kontakt.io’s IoT Device Management to automatically onboard, provision, and manage their IoT ecosystem. Connect our BLE-enabled devices and tags alongside your existing network components, minimizing manual work and reducing time-to-market.
Minimize time, complexity, and cost spent managing thousands of IoT devices
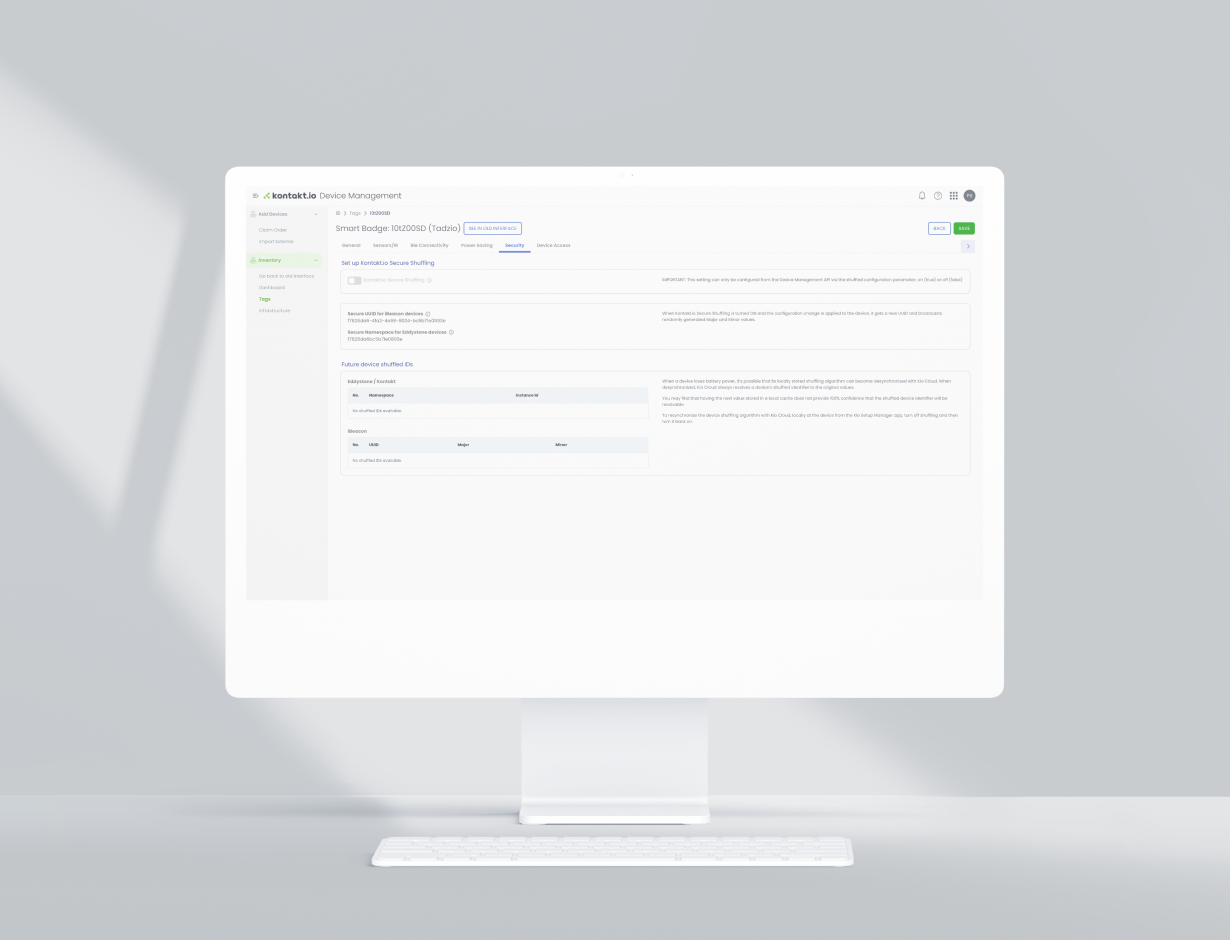
Enforce IoT edge-device security to prevent malicious attacks on local-area network
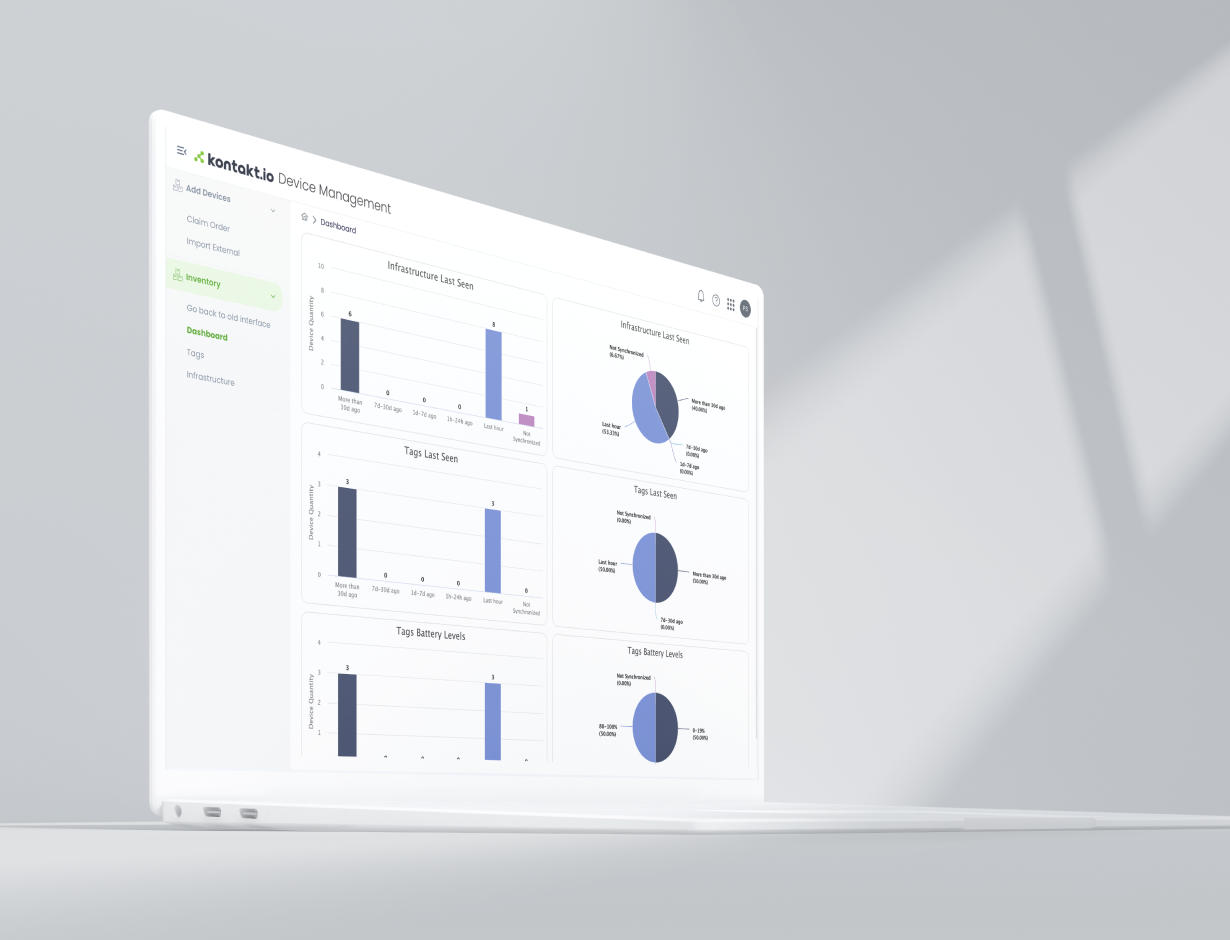
Monitor and receive real-time alerts on sensor, tag, gateway, and wayfinding infrastructure issues
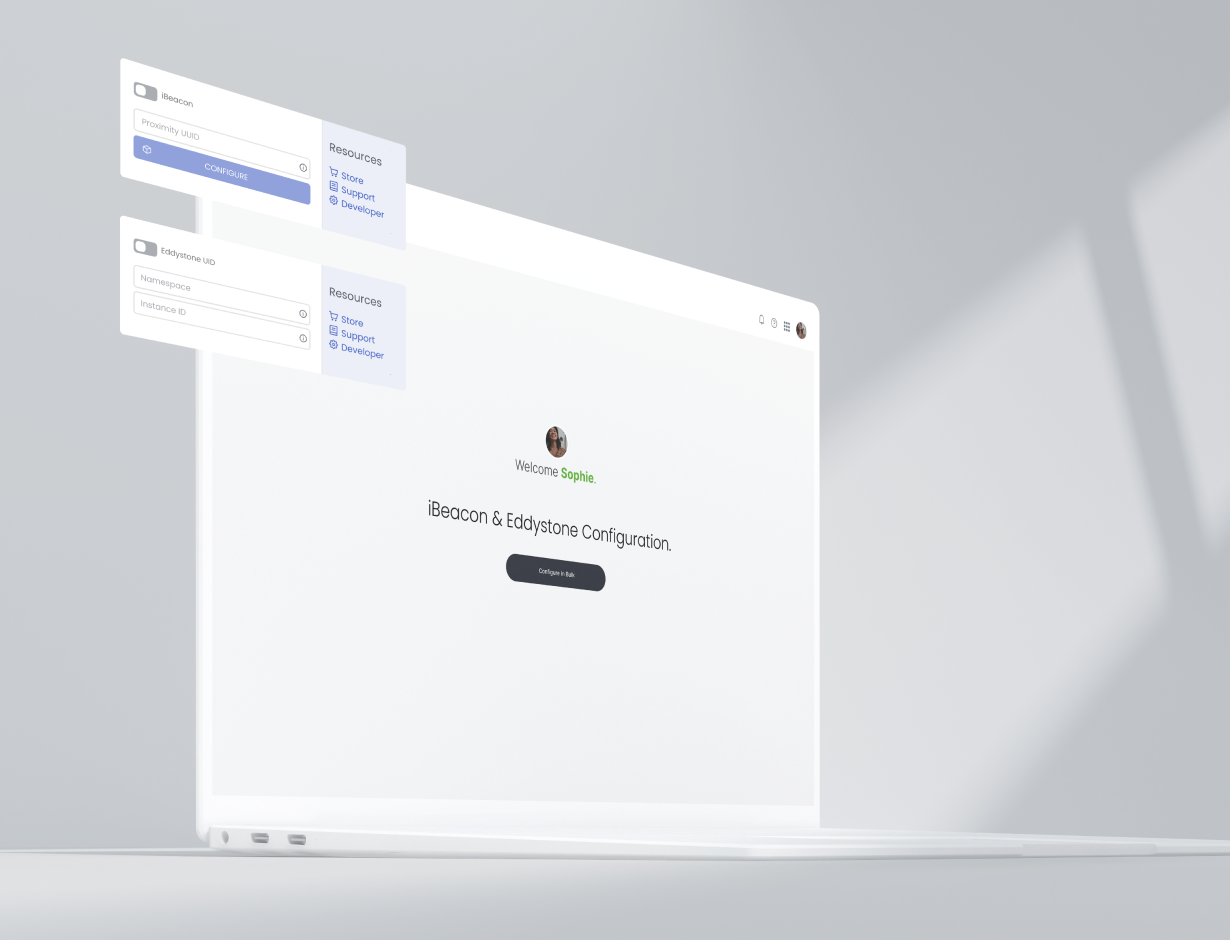
Manage your organization’s location hierarchy by integrating multiple device feeds on the cloud